Wi-Fi trackers provide valuable information such as: people path, crowd size, visit duration, and frequency to retailers and businesses. However, Wi-Fi trackers are also a threat for citizen’s privacy. Periodically Wi-Fi enabled portable devices broadcast a unique identifier in the clear. By collecting this identifier, it is possible to detect a visitor, triangulate their position, and track their movements. Several Wi-Fi tracking systems are already deployed in retail places where they can provide information on the customer’s habits. Retailers and businesses can record the whereabouts of any individual that happened to carry a device with Wi-Fi turned on; Therefore, they can monitor the activities of a large fraction of the population. Retailers and businesses do not need any consent of the users, and it is impossible for the consumer to know if tracking is performed.
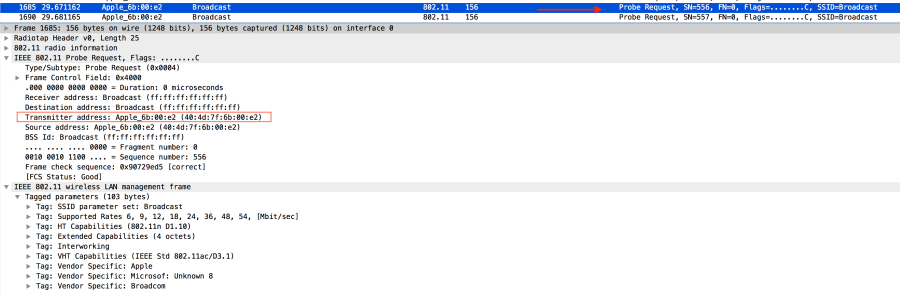
Wi-Fi tracking systems are keeping track of people’s whereabouts by capturing the messages broadcasted by their Wi-Fi enable device. Smartphones use an active service discovery mechanism to search surrounding access points. In active service discovery mode, a smartphone periodically broadcast probe request frames. Upon reception of a probe request, an access point (AP) replies with a probe response, thus declaring its presence. The image below shows my iPhone mac address captured using Wireshark:
Wi-Fi tracking systems can track visitors in a retail space, because people’s smartphones are periodically broadcasting a unique identifier (MAC address). The Wi-Fi tracking systems record the MAC address, time-stamp, and sensor’s data for each received probe request. From this information, the Wi-Fi tracking systems can deduce the presence and the path of a Wi-Fi device across the area covered by the sensors.
Most Wi-Fi tracking systems do not fully disclose in their privacy policies how the data is collected, transferred from the sensors to the server, kept anonymous, and stored. Most Wi-Fi tracking systems companies rely on hashing the mac addresses method to anonymize MAC addressees in their databases. Nonetheless, how secure is our data if the database is compromised? According to French researchers Demir, Cunche, and Lauradoux, the hash-based anonymization use in Wi-Fi tracking systems can be defeated using free software tools such as, hashcat, in less than a day. They recommended to encrypt the MAC addresses entries obtained from a chain of hash with a master key. This master key is used once by the storage server and its known only by the entity computing the statistics. For each entry, a new key is generated using a cryptography one-way function and the previous key is erased. If a session key is compromised, the hacker will only know a single entry of an individual, instead of having access to all the entries in the database. Another element not mentioned clearly by Wi-Fi tracking companies is how individuals can opt-out when in proximity to the sensors. Retailers and businesses argue they can use the collected data to better tailor services to consumers; however, privacy, data protection, and human rights remain a significant concern.
Demir, L., Cunche, M., & Lauradoux, C. (2014, June). Analysing the privacy policies of Wi-Fi trackers. In Proceedings of the 2014 workshop on physical analytics (pp. 39-44). ACM.